We knew cybercrime was bad, but seeing the numbers in Microsoft’s latest report is enough to make anyone double-check their password strength. According to Microsoft’s Digital Defense Report released on October 15, ransomware attacks have skyrocketed over the past year, with hackers throwing 600 million threats daily at Microsoft’s customers. But before you go burying your phone in the backyard, there’s some good news: advancements in automatic attack disruption have made it tougher for these attacks to reach the encryption stage.
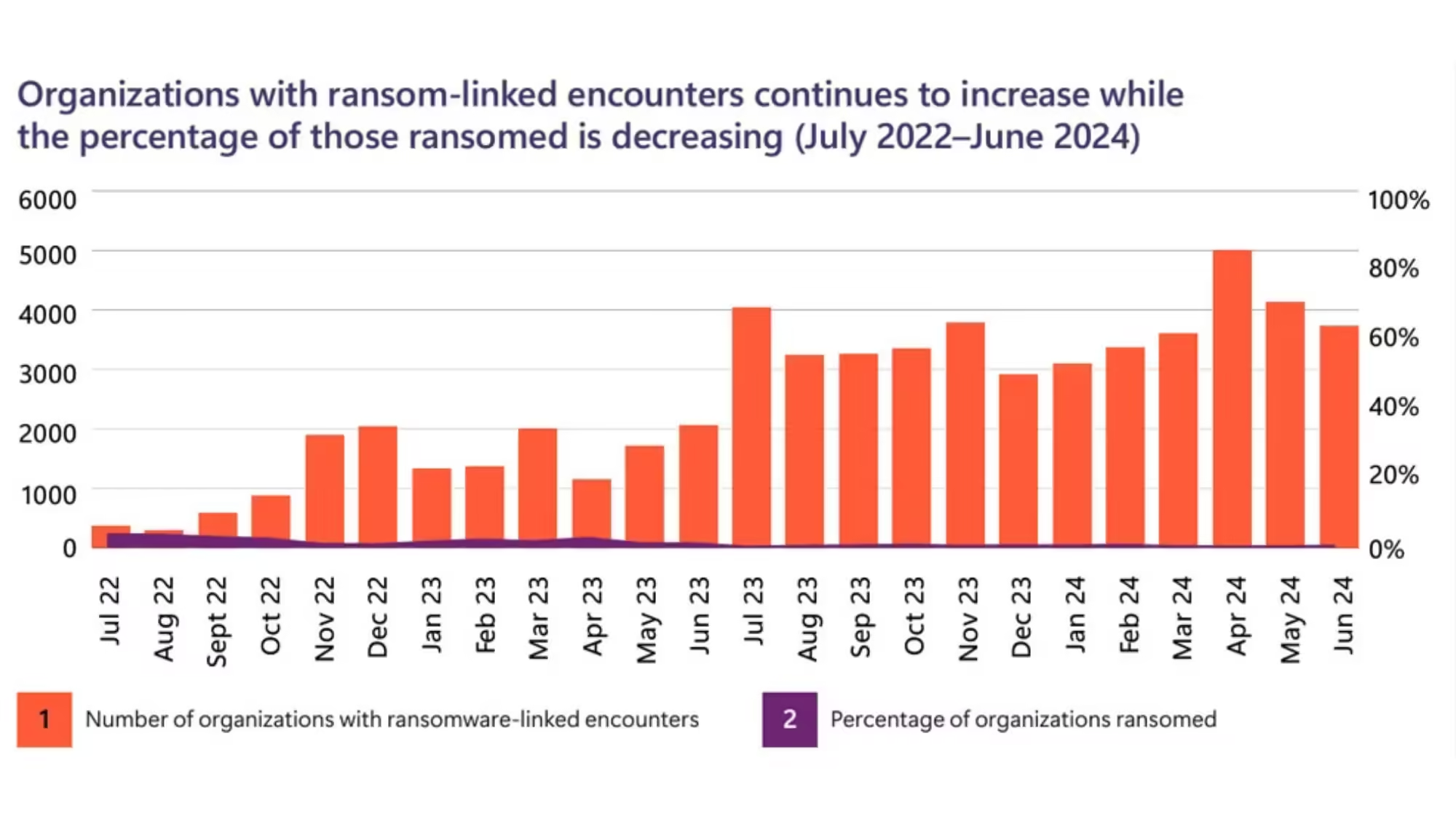
Let’s break it down: ransomware attempts jumped by a massive 2.75 times in the past year, but the number of attacks that actually resulted in locked files and ransom demands dropped by a third. It’s like cybercriminals are shooting more shots, but hitting way fewer goals.
What’s in the Hacker Toolbox?
The report revealed that Microsoft is tracking more than 1,500 threat groups, including 600 state-sponsored hackers, 300 cybercrime rings, and even shady groups running influence operations. But ransomware gangs like Akira, Lockbit, Play, Blackcat, and Basta are the stars of this rogue show, responsible for over half of all ransomware attacks.
The classic moves these criminals pull? Social engineering (i.e., tricking people into doing something dumb), stealing passwords, and exploiting unpatched apps or operating systems. Once they’re in, they often install remote monitoring tools or disable your security software like it’s no big deal. Microsoft noted that 70% of successful attacks involved hackers encrypting data remotely, and a shocking 92% targeted devices that weren’t being actively managed by IT teams.
But that’s not all they’ve got up their sleeves. Hackers have been busy launching a wide variety of attacks, including:
- Infrastructure attacks (think critical services like power grids)
- Financial fraud
- E-commerce theft (stealing your credit card info without needing the physical card)
- Identity theft and social engineering scams (99% of these were password-stealing schemes)
- SIM swapping
- Deepfakes (because why not make the internet even more confusing?)
- Impersonation scams
- Credential phishing (especially via sneaky PDFs or HTML files with malicious links)
- DDoS attacks, which even caused a global outage earlier this year
- Tampering with antivirus software (Microsoft’s own Defender XDR recorded 176,000 instances of this)
It’s like a hacker’s wild buffet, and your device is the main course.
Nation-States and Cybercrime: Frenemies?
Here’s where things get more complicated. Microsoft found that nation-state hackers and good old-fashioned cybercriminals are increasingly sharing tools and tactics. In fact, financially motivated hackers have started using cloud identity compromise attacks, something that was once the domain of government-backed actors. It’s like watching secret agents and bank robbers team up for a heist.
The report highlighted the fact that major threat groups from Russia, China, Iran, and North Korea are getting in on the action. Sometimes, these nation-states turn a blind eye to financially motivated actors operating within their borders. Other times, they outright use them to further their own goals. It’s a cybercriminal partnership of the worst kind.
Tom Burt, Microsoft’s corporate VP of customer security and trust, explained that there’s a growing overlap between nation-state operations and cybercrime. He pointed out that some countries actually profit from this activity or don’t bother to crack down on it, which makes the problem even harder to deal with.
Former NSA cybersecurity expert Evan Dornbush offered his two cents on the issue, noting that criminals are earning more money than ever from these cyberattacks. “The government makes up only 12% of the targets, with the private sector taking the brunt of the damage,” he said. The top targets? IT, education, government, think tanks, NGOs, and transportation.
AI: The Newest Player in Cybercrime
Generative AI is shaking up the cybersecurity landscape — for both hackers and defenders. Microsoft’s report dives into the growing use of AI in cyberattacks, from AI-powered phishing scams to deepfakes and even résumé swarming (yep, fake job applicants are a thing). While AI is helping defenders automate their responses, it’s also giving attackers new ways to cause chaos.
Microsoft warns that companies need to be extra careful with how they handle AI, especially when it comes to protecting sensitive data. They recommend applying strong data governance policies to mitigate the risks. Even though many governments agree that AI security is important, they’re all going about it in different ways, which complicates things even more.
Burt emphasized that the sheer number of attacks needs to be reduced through a combination of better cybersecurity measures and government action. “The industry must do more to block attackers,” he said, “but we also need governments to impose real consequences to discourage the most harmful cyberattacks.”
What Can Companies Do to Stay Safe?
Microsoft’s report doesn’t just shine a light on the growing threat landscape. It also offers some solid advice for organizations looking to protect themselves. Here are a few key takeaways:
- Disrupt attacks at the technique layer: This means implementing policies like multi-factor authentication (MFA) and reducing your attack surface.
- Use secure-by-default settings: For instance, make MFA mandatory for all users.
- Strengthen password protection: Come on, we’ve been saying this for years.
- Test security settings in a safe environment before rolling them out live.
- Classify and label sensitive data, and use data loss prevention (DLP) policies around high-risk data and users.
Microsoft also mentioned their Secure Future Initiative, which was launched in response to the Chinese hacking of government email accounts in July 2023. It’s their big move toward bolstering the security of their services and products in a world where cyber threats are evolving at warp speed.
In short, the future of cybersecurity looks like a battleground, with both sides continuously leveling up. Hackers are getting more creative, and organizations need to stay one step ahead — or risk becoming the next headline.


